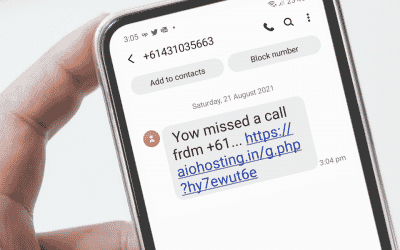
As most everyone knows, cyber-crime has increased massively over the last year or two. Dodgy emails have been the weapon of choice for criminals. But now a new threat is growing, catching out victims via SMS text messages on our phones. Flubot, having done the rounds...
Category
Cybersecurity
Why Use a Password Manager?
Why Use a Password Manager? In these days of increased cybercrime, a good password (as well as other defenses), is extremely important. A common problem with passwords though is that it’s hard to remember all of them. This means that many people end up with one or two...
Don’t Use The Same Password – A cautionary tale
Don't use the same password Don't use the same password should be your company's mantra on creating safe access to each account. On May 7 of this year Colonial Pipeline based in Houston, Texas, suffered a ransomware attack that crippled its operations. Colonial...
One Day Backups May Save Your Business
One Day Backups May Save Your Business One-day backups may save your business from big trouble if you had been keeping file backups. There was a story the other day about a company that was hit with a ransomware virus and all their data was encrypted. Because they...
5 New Year’s Resolutions for Your Computer
Running the Best Security Software Most computers today run at least some form of basic antivirus. In the modern-day however, threats have evolved to be more sophisticated, more damaging, and much more common. Ransomware, malware, phishing, and zero-day attacks all...
Keep Your Firmware Safe and Secure
Most of us can differentiate between hardware and software. But how many know what firmware refers to? More importantly, is your business securing its firmware against security vulnerabilities? Your business knows it needs to keep its operating systems (OSs) up to...